Italy
Researcher (scientific/technical/engineering)
Date of the expedition
From 05/04/2024 to 05/07/2024
Selected Track
Open Ideas
Project title
GUARD1
Host Organization
International Computer Science Institute
Media
Biography
Alessandro Palumbo is an Associate Professor at CentraleSupeléc and an Associate Researcher at IRISA Lab, Inria, and SUSHI Team.
From April 2024 to July 2024, he will be a Visiting Researcher at the International Computer Science Institute (ICSI), University of California, Berkeley.
His research focus is Hardware Security. In particular, his interests include hardware acceleration of networking functions and CPU microarchitectures, with particular emphasis on Machine Learning techniques and Probabilistic Data Structures to guarantee security and reliability in microprocessor-based systems in both FPGA and In-Memory Computing scenarios.
Project Summary
Building a platform (on FPGA) integrating a Core and a Hardware Security Module (HSM). It will check if Microarchitectural Side-Channel Attacks (MSCA) are running the Core. The HSM will be programmable to set which MSCAs we want to detect and which microprocessor features have a look to detect such attacks.
This research work will be useful in protecting cores against attacks and signaling which features are the most relevant to detect the attacks.
Key Result
Microprocessor-based systems implemented via the Guard1 paradigm will be attack-free. Considering an attack (even a new one), choosing the features to observe, programming Guard1 will monitor the Microprocessor running and detect the possible attack. Guard1 is a hardware circuitry, so a malicious user cannot “uninstall” it to run its attack on the Microprocessor. We expect to design a platform to run experiments to evaluate its vulnerability and protecting from those.
Impact of the Fellowship
Starting from the expected impact described in the application form. For instance:
- The problem we want to solve and the target group or area that will benefit and how
Exploitation (unintended) for information leakage of computing devices or implementations to infer sensitive information. By looking at Microprocessor features, apparently not related to its program run (i.e. execution times, power consumption, memory footprints…) an attacker may leak sensitive information. Many attacks in the state-of-the-art perform such leaking looking from side-channel features (i.e. Spectre and Meltdown). These attacks operate by looking at microprocessor-level features (close to the physical circuit, like cache access times). It’s extremely challenging for software to obfuscate circuit-level vulnerabilities and detect attacks looking for low-level features.
- The innovative features of the project
To the best of my knowledge, to state the art, there are a couple of microprocessor-based systems integrating HSMs. On the other hand, many software solutions are present. Why do we need HSMs to protect against attacks? Aren’t software solutions (software antiviruses) enough? Why do we need HSMs to protect against Microarchitectural Side-Channel Attacks (MSCAs)? Aren’t software solutions (software antiviruses) enough? HSMs are essential because it’s extremely challenging for software to detect circuit-level threats. They operate at the same level as these threats, making them well-suited to detect and defend against such low-level attacks. If an attacker manages to inject something referred to as a MSCA, he/she could potentially compromise and disable the software defenses protecting the microprocessor. In contrast, an attacker would likely need physical access to the microprocessor where the HSM is integrated to sabotage it, making it a more resilient security measure against certain types of attacks.
- The Project Innovation
It has been demonstrated that it is possible to detect malicious software runs by looking at Microprocessor Performance counters. Hardware Security Modules (HSMs) have been implemented to counter microarchitectural side-channel attacks. To the best of my knowledge, it is state of the art; it is missing a HSM implemented in a soft core looking for attack signatures based on Microprocessor features. It has been demonstrated that by looking at some features of bitstream implementing Microprocessors (#LUT, #FFs, Circuit Worst Negative Slack, etc.), it would be possible to detect undesired circuit modification (i.e., Hardware Trojan Horses) on the bitstreams. The Guard1 project aims to protect from Microarchitectural Side-Channel Attacks via machine learning approaches by looking at the features of the Microprocessor implemented on the FPGA..
- Expected impact
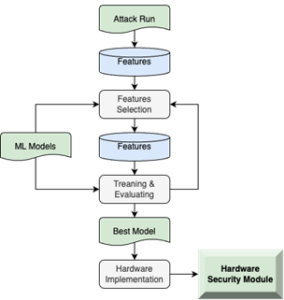
Microprocessor-based systems implementing the Guard1 paradigm will be attack-free. Considering an attack (even a new one), choosing the features to observe and program the HL&D system will monitor the Microprocessor running and detect the possible attack. Guard1 consists of a hardware circuitry implementation, so a malicious user cannot ”uninstall” it to run its attack on the Microprocessor. The workflow is reported in Figure 1. In particular, an attack will be chosen to detect and run on the Microprocessor. After (and during) such program execution, it is possible to observe some features, i.e., performance counter values, power consumption traces, execution times, temperature traces, etc. Depending on their nature, such estimations could be done via tools or physical measurements. To have more reasonable values, features like temperature and power consumption traces will be measured on the board of the FPGA implementing the target microprocessor. On the other hand, performance counter values will be extracted by tools. Later on, all the collected features will be inputted into a Machine Learning model. Offline, it will filter and select the most relevant features to observe (the attack signature) to detect the attack.
When “the best” Machine Learning model is found, the Hardware Security Module will be implemented based on that model and integrated into the target Microprocessor. What if a new attack comes? Just repeat the workflow.
The final expectation of this research project is to design an open-source platform integrating a Microprocessor and an Hardware Security Module to run experiments to evaluate the core vulnerabilities and protect from those. This methodology could improve the Microprocessor market and its supply chain. The integration of Hardware Security Modules in Microprocessor-based systems could become part of the System-on-Chip (SoC) supply chain. This new paradigm consists of innovation and will produce competitive products (i.e., third-party intellectual proprieties) for the digital and soft-core Microprocessor market. Thinking about a System Integrator wanting to build a SoC, he needs to integrate different circuit modules and third-party intellectual proprieties to build its system: core, memories, hardware accelerators, and potentially, also a Hardware Security Module for attack detections. Nowadays, existing industries with expertise in the design of memories, hardware accelerators, etc. Consequently, new industries specializing in HSM designing can arise, giving birth to new job opportunities for engineers, designers, maintainers, and project managers.
The research project goal is to implement hardware modules that are as lightweight as possible. I will proceed to implement low-overhead architectures with respect to the Microprocessor in terms of power consumption, execution times, and area occupation.
To the best of our knowledge, in the state of the art, there is not much study going into hardware-based methodologies details to detect (and/or boycott) malicious software.

